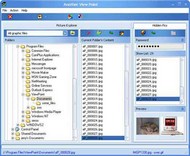
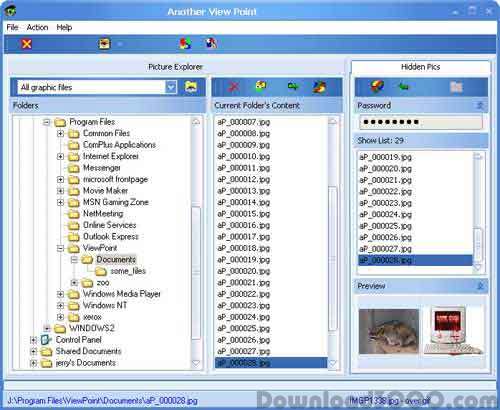
To avoid any suspicion about your secret your file, it is hidden inside another file (your file is encrypted by the most modern and strong cryptographic algorithms) and the encoding program is also hidden inside another absolutely neutral (but useful) program. As a result your computer has neither secret files nor obvious programs for encrypting information or secrets. The hidden pictures are viewed with the same speed and comfort as usual ones.
Publisher description
Everybody has a right to privacy and business secrets. You have a little secret. It is saved as a graphics file (illustration, photo, scanned document, etc.). You do not want anyone to know your secret and anyone to suspect you have a secret. ViewPoint allows the user to conceal details (of their private life or business) from unauthorized viewers. If the user needs to conceal confidential pictures, he can use various programs for protection. Meanwhile these programs do not allow use of the concealed data as easily and safely, as you can with normally unprotected files. Our program is not available obviously. It is hidden inside another, absolutely usual and neutral program (Another ViewPoint inside ViewPoint). Confidential files are not kept as hidden files. They are kept inside carriers - usually pictures. The pictures (carriers) themselves are not distorted. Any program that can be used to view pictures will show the carrier's content only. The above mentioned features are very important psychologically. When the secrets or their traces are absent, the computer's owner is above of suspicion. As a result nobody will try to reveal their secrets. When you review confidential information, the program does not leave any traces on your computer (almost all similar programs create, for example, temporary files). Windows only knows about the history of neutral files (carriers) being viewed. To encrypt data before hiding it uses the latest strong cryptography methods known, e.g. AES. The size of hidden pictures is not limited. If you know the right password, the hidden pictures are viewed with the same speed and comfort as usual ones. The program allows restoring hidden files and clearing the carriers along with their original file names. If this program had deleted the files they could not be restored. Any special software or hardware is powerless to restore them. This program may be used for safe information exchange via Internet or mobile communications providers.
Related Programs

CyberSafe Files Encryption 2.1.5.1
Protect data with file encryption tools.
File Renamer to rename files, renaming files in ba 9.0
Rename files easily with this superior file

Split Text Files Into Multiple Files Software 7.0
Split text or HTML files into smaller files.

1 Click Encrypt File Folder Encryption 1.4.1
Secure files and folders

DVD,Apple iPod MP4 files, Sony PSP MP4 files, Cell 6.0
Jasonsoft DVD to iPod PSP 3GP PPC MP4